Stop TrueCrypt from Leaking
Mi 11 Dezember 2013 by Andreas HüwelTrueCrypt Leaking
With using TrueCrypt and container files your system leaks and bookmarks your recently used containers!
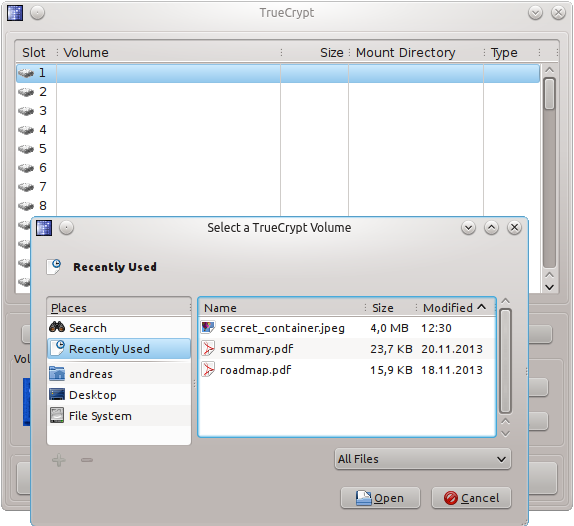
Put shame on them, since TrueCrypt GUI even offers a checkbox to Never save History. But when it comes to step 15 of their tutorial shit happens: Whether you want or not, the selected file will be bookmarked inside an xml file. For my Ubuntu it is this:
$HOME/.local/share/recently-used.xbel
An attacker with access to your home folder (physically or via network) could use the recently-used file to easily see where your actively used TrueCrypt containers are, and thus you
-
spoil any plausible deniability
-
present where your precious encrypted containers are
I am very sad, because this issue is open, known and yet unsolved for some long time. Indeed I am very pleased to just see that The TrueCrypt Audit will be launched. You still can support it, so maybe just check it out yourself? Maybe there we get a true solution. Someday.
Until that happens people suggest a manual clear file workaround and also I see many non working workaround-suggestions like this or this out in the wild. Latter not only just won’t work but also give a false sense of security. Either you try to switch off the recently used feature for all apps - and how (or if at all) thats done is very system specific. On many linux distributions TrueCrypt runs with root powers (via sudo or special bit set). All workarounds fiddling with locking the recently-used file just not work. TrueCrypt running as root will override such efforts and still create the recently used bookmarks. So as last resort one can turn that file into an empty folder and put it root-and-readonly.
Workaround Script
Besides the all known TrueCrypt security concerns I myself also want to do some steps to Take Back the Internet. Here my first aid for this one issue.
This open source bash script truecrypt_wrapper.sh is a workaround for TrueCrypt on linux, helping a bit against the described serious security problem of TrueCrypt.
Just call this wrapper-script instead of TrueCrypt. It will call the installed TrueCrypt binary and do some cleanup.
This script was inspired by How To: Cover you tracks with truecrypt in gnome and TrueCrypt Clear Recent Documents List. I not only want to see workarounds hide in a forum and age silently. Instead lets make a next step and make it an open source project so everyone can colaborate at this issue.
Spread the news!
Please tell people of this security issue! Don’t leave people in the lurch when they already put effort using security tools but with a false sense of their actual security situation!
Caveats
Always remember: This is not a fix, but only just a workaround a severe security issue with TrueCrypt!
please check out the README.md for more.
How about a True Solution?
Actually the bookmarking is part of the GUI, and happens when doing select file. Inside the file browser you select your container file and then when pressing “OK” you trigger the bookmarking. That recently-used stuff itself is not part of the TrueCrypt code, but of your Desktop environment (TrueCrypt GUI uses GTK).
I think that a pure solution would be to use an independent implementation of an own file-selector, not using the one offered by the environment. So no one would trigger the bookmarking stuff. Sure: Loosing some comfort and integration, like some of this alien looking and behaving java apps that have their own design.
Maybe one could also solve the problem with statically linking to a separatedly compiled system-file-selector-library, compiled without that bookmarking stuff. Then we would have won back the good integration into desktop environment that TrueCrypt currently has.
Recently Used - Brute Forced
I just want to make you aware: So as soon as someone really has unlimited access to your machine (or a dump of your drive for e.g. forensic analysis) such list of “recently used” can be created.
Once I stumbled over this nice one-liner, alas the site seems now offline. So I just can scrape from my memory… I think it looked something like this:
$> find ~/{Documents,Desktop,Downloads,Music} -ctime -7 -type f -exec bash -c 'select f;do [[ -n $f ]]&&xdg-open "$f"||exit;done' _ '{}' +
ctime -7 means “seven days old”.
You are presented the list of found files,
then you may select which you want to open.
xdg-open will try to open with adequate tool for that file-type.
I definitely think it is a huge difference: Actively leaking myself regularly used TrueCrypt containers into one nice file, so everybody just can sneak in and check it out. Or someone noisily crunching through my drive with a brute force filechecking attempt - a time and load consuming process that easily can be detected. Alone such increased risk of being detected surely will keep many from doing, or citing Bruce Schneier: Assume that while your computer can be compromised, it would take work and risk on the part of the NSA — so it probably isn’t.
So in the end, how else could it be, it all depends on your security policy - what risk do I fight and what do I accept.
Don’t panic - brain on…
